FireEye Trellix Helix
API creation and configuration
-
On the Helix Homepage click on the Profile and Identity Access Management Console
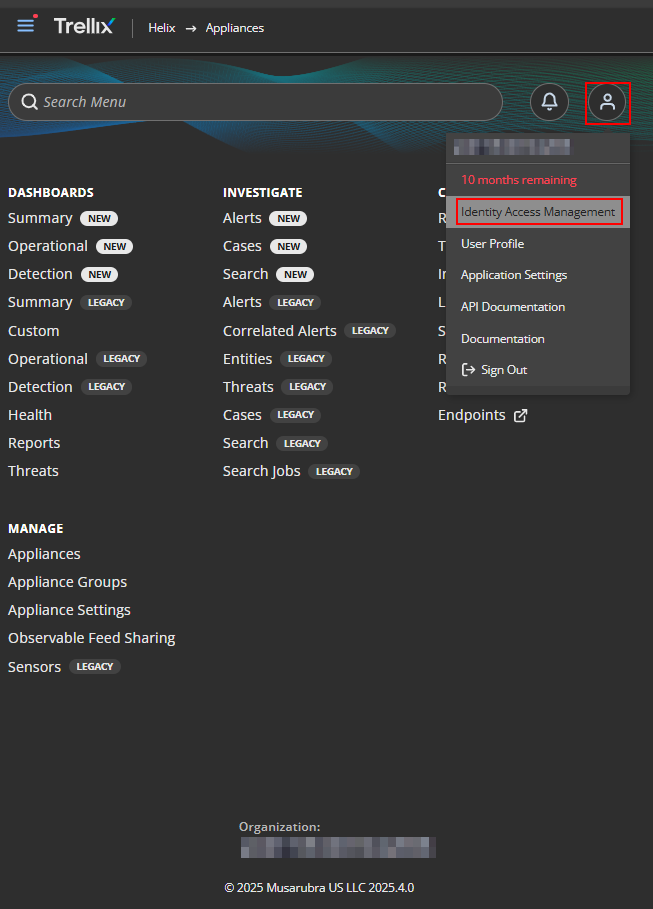
-
On the IAM page move under “API Keys” and Create a new API Key
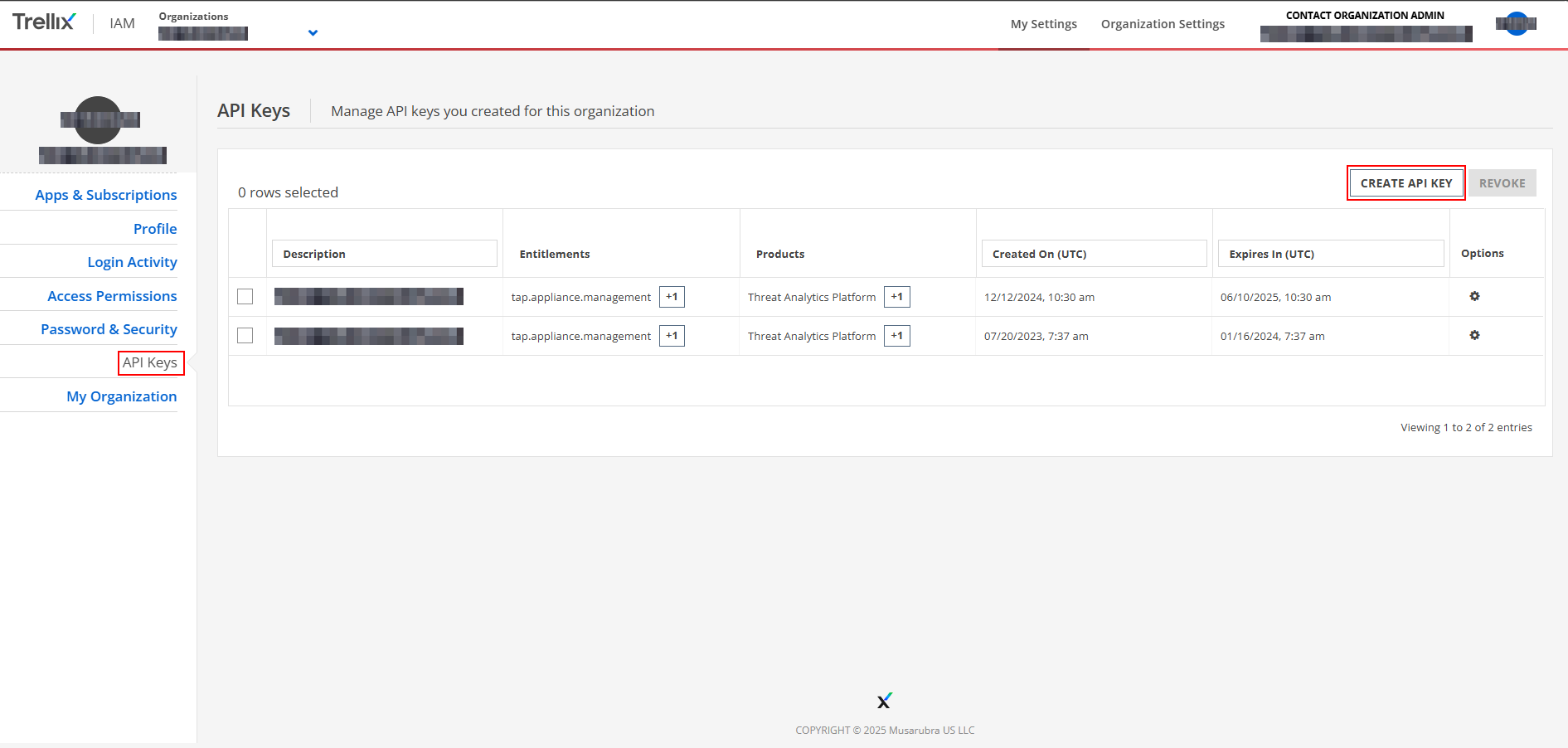
-
Check “API Key with entitlements”, with expiry of 1 year and as Products “Threat Analytics Platform”
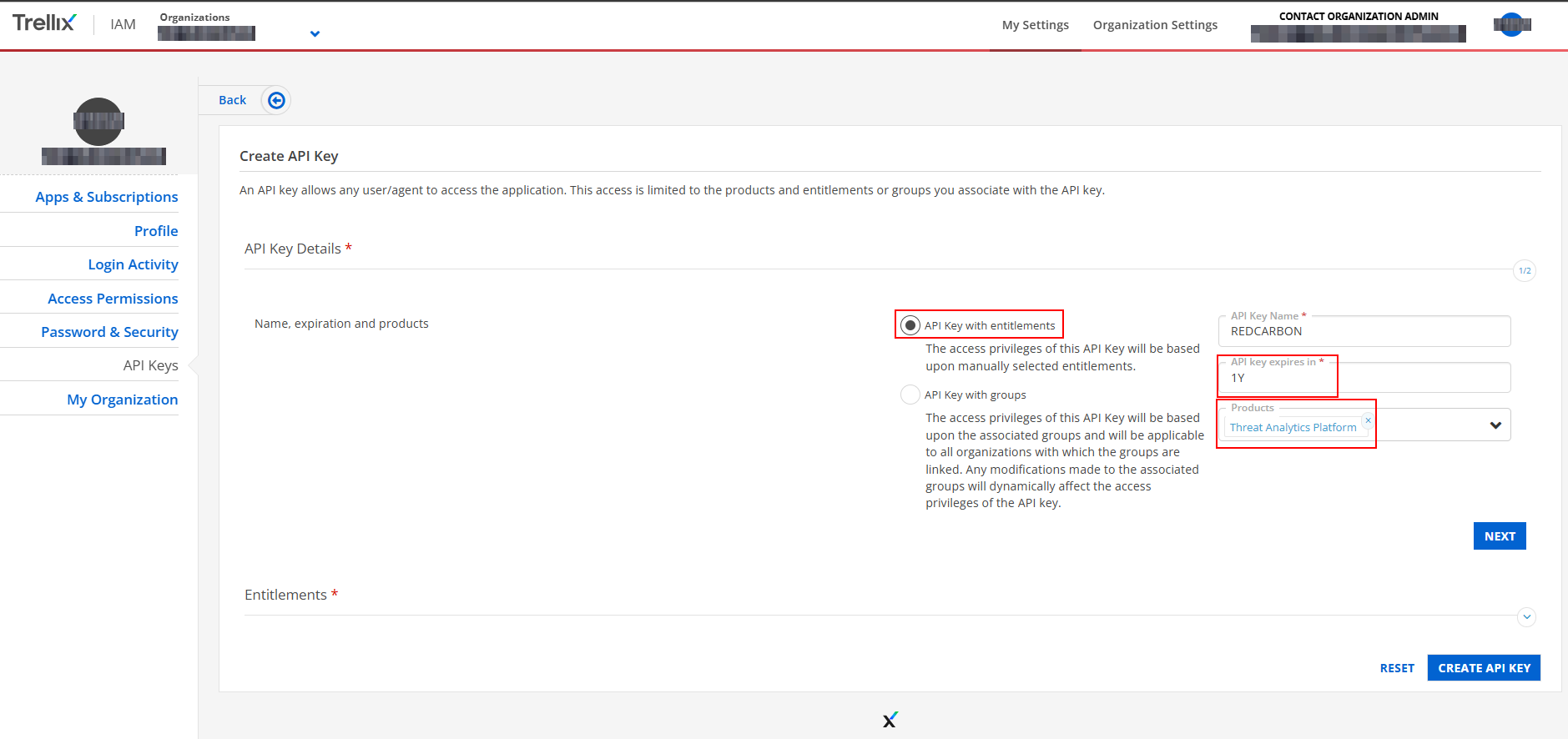 >
> -
For the entitlements select “tap.alerts.browse”, “tap.alerts.read”, “tap.alerts.edit”
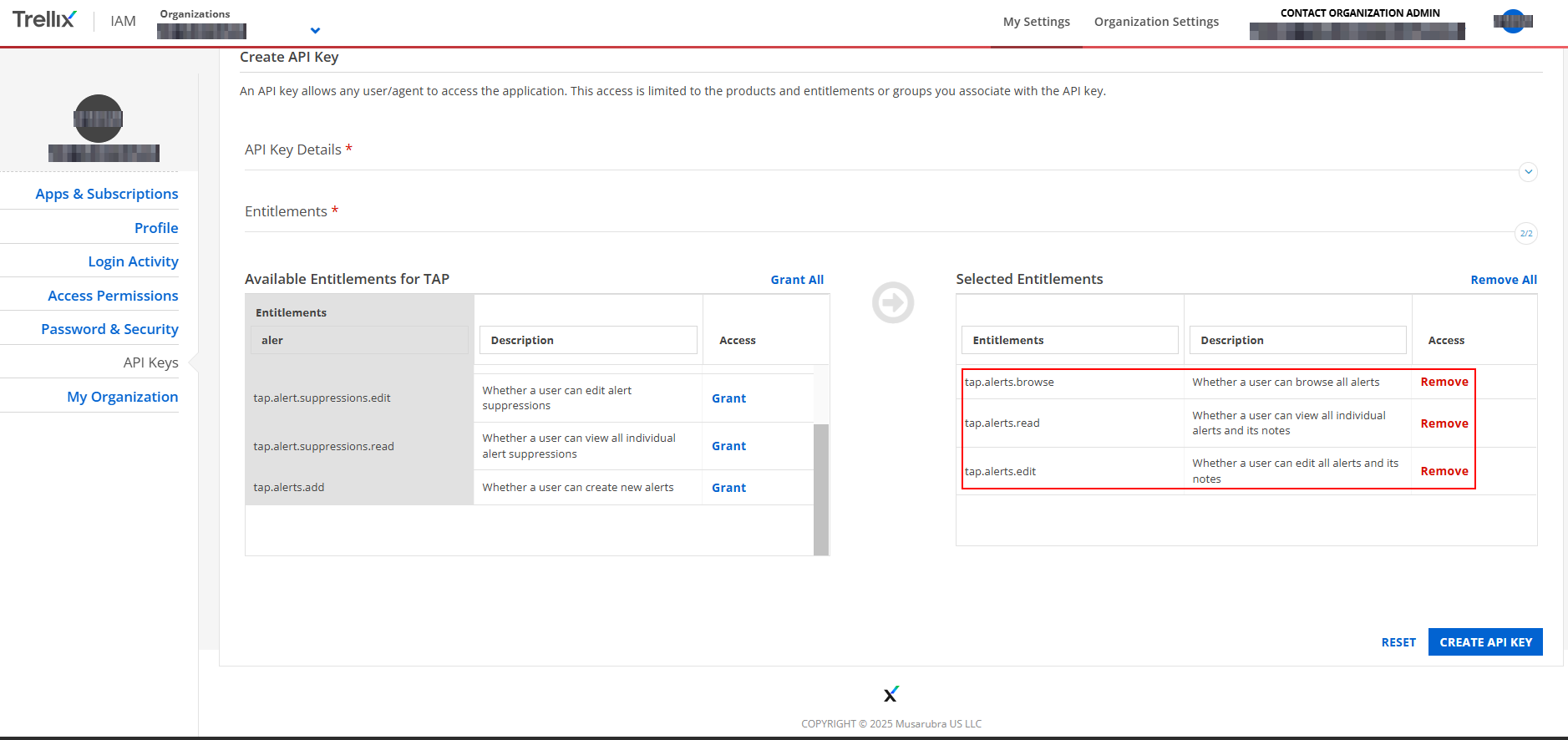 >
> -
Copy the API Key to the RedCarbon integrations page
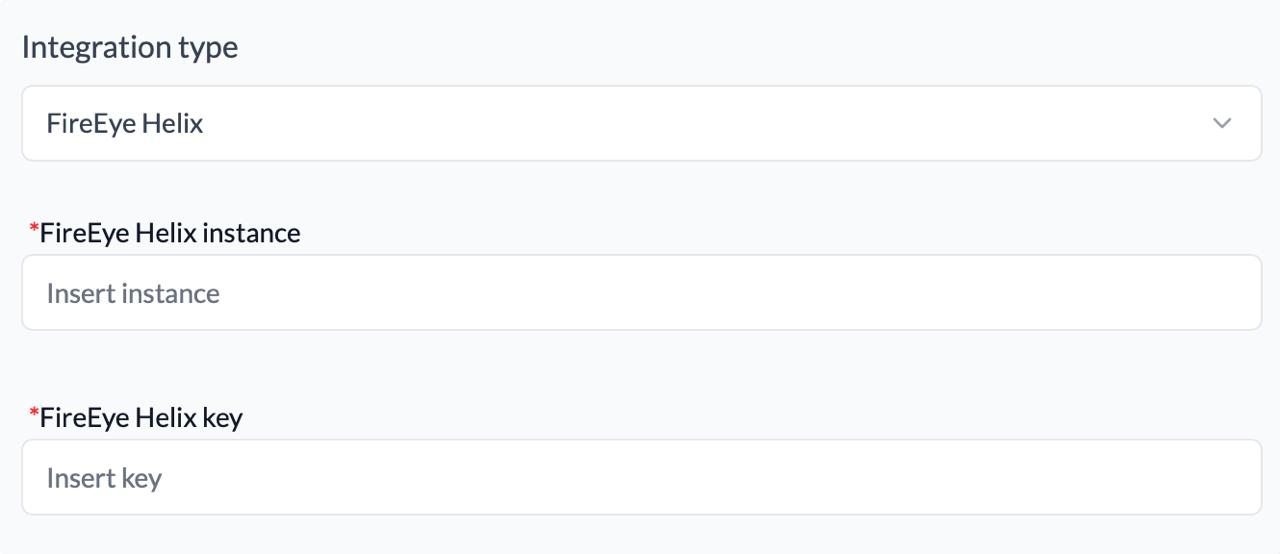 >
>
Mapping
Classification
| RC Alert Logic ID | Description | RC Classification | Notes |
|---|---|---|---|
| H-1A | |||
| H-2A | OFFICE 365 ANALYTICS [Abnormal Logon] | office_365_analytics | |
| H-3A | OFFICE 365 ANALYTICS [Consent To Application With Offline Access] | office_365_analytics | |
| H-4A | OFFICE 365 [User Added Credentials to Service Principal] | office_365 | |
| H-5A | OFFICE 365 [Mail Forward Attempt] | office_365 | |
| H-6A | OFFICE 365 ANALYTICS [Inbox Rule Delete] | office_365_analytics | |
| H-7A | OFFICE 365 ANALYTICS [Inbox Rule Mail Forward] | office_365_analytics | |
| H-8A | OFFICE 365 ANALYTICS [Brute Force Success] | office_365_analytics | WINDOWS ANALYTICS [Brute Force Success] it is correlated? |
| H-9A | OFFICE 365 [Brute Force Attempt by IP] | office_365_analytics | |
| H-10A | OFFICE 365 METHODOLOGY [Strong Authentication Disabled] | office_365_methodology | |
| H-11A | OFFICE 365 [Malware Detected] | office_365 | |
| H-12A | OFFICE 365 [Suspicious File Type Uploaded] | office_365 | |
| H-13A | OFFICE 365 [Multiple Secure Links Created/Used] | office_365 | |
| H-14A | OFFICE 365 [Tor Authenticated Activity] | office_365 | |
| H-15A | VPN ANALYTICS [Abnormal Logon] | vpn_analytics | |
| H-16A | FIREEYE NX ALERT [SmartVision-Event] | fireeye_nx_alert | |
| H-17A | WINDOWS METHODOLOGY [Group Add - Administrators]WINDOWS METHODOLOGY [Group Add - Domains Admins] | windows_methodology | |
| H-18A | OFFICE365 [Tor Failed Logon] | office_365 | |
| H-19A | WINDOWS ANALYTICS [Brute Force Success] | windows_analytics |
Other Open Points
- Currently, we do not handle the type
OFFICE 365 [Multiple Owner Changed From Same User]but it is used inside the platform.
Severity
| Original | RC Severity | Rebased |
|---|---|---|
| low | 10 | 5 |
| medium | 40 | 20 |
| high | 70 | 35 |
| critical | 90 | 45 |
| DEFAULT | 40 | 20 |