Microsoft 365 Defender
Integration
The integration is working with the product Microsoft Defender XDR, the unified enterprise defense solution that automatically aggregates and analyzes signal data from multiple sources, for example, anomalous behavior from Microsoft Defender for Endpoint or a suspicious sign-in from Microsoft Defender for Identity. It then correlates the data into an incident that represents an attack and provides easy investigation and response across endpoints, identities, emails, and applications.
References
- What is Microsoft 365 Defender? - Training
- Microsoft 365 Defender incidents APIs and the incidents resource type
- Microsoft 365 Defender APIs creation
API creation and configuration
Be aware that for APIs creation you need to ask azure, because we don’t have permissions to do that.
-
Log on Azure with a user that has the Global Administrator role
-
Navigate to Azure Active Directory > App registrations > New registration
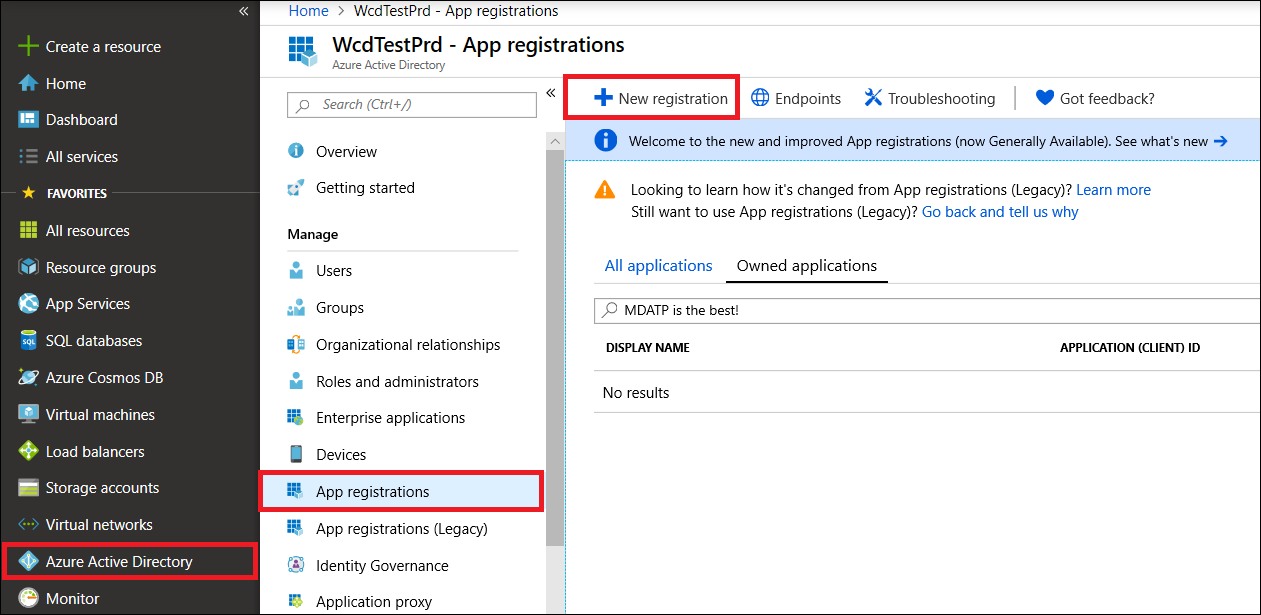
-
In the registration form, choose a name for your application, and then select Register
-
To enable your app to access Defender for Endpoint, on your application page, select API Permissions > Add permission and select the following permissions
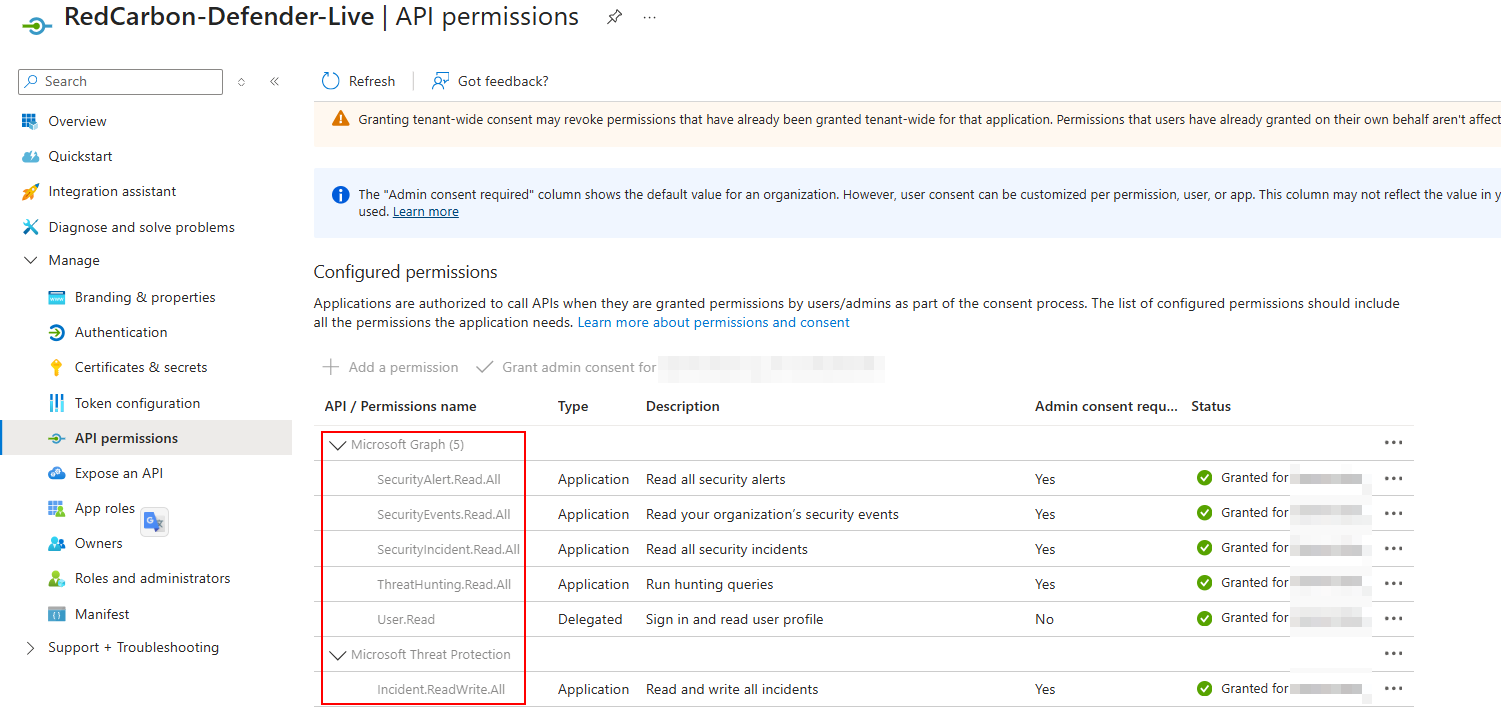
-
Select Grant consent
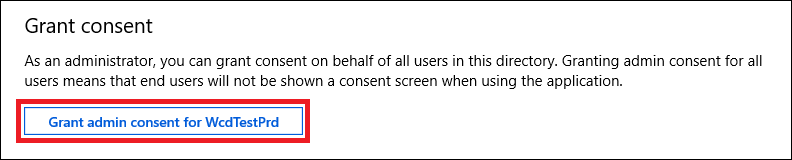
-
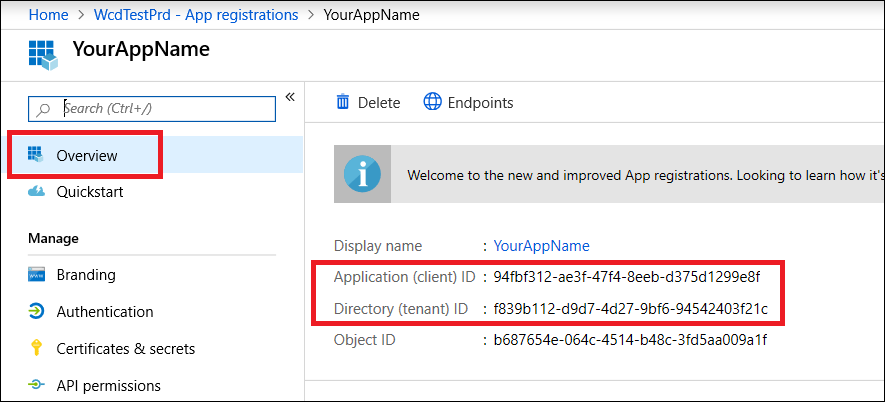
Write down your application ID and your tenant ID. On your application page, go to Overview and copy the following.
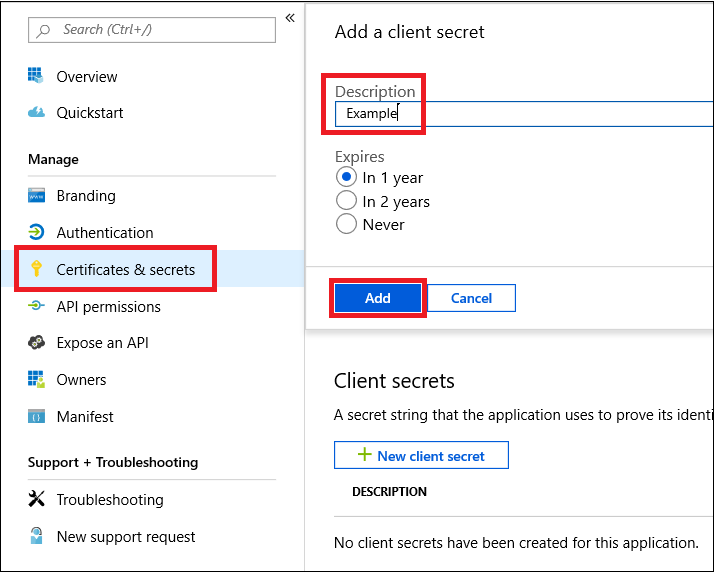
-
Copy all the data into RedCarbon integrations page
Mapping
Severity
| Original | RC Severity | Rebased |
|---|---|---|
| Low | 10 | 5 |
| Medium | 40 | 20 |
| High | 70 | 35 |
| Critical | 90 | 45 |
| Informational | 0 | 0 |
| UnSpecified | 0 | 0 |
| DEFAULT | 40 | 20 |